Everyone thinks security. Keep the bad guys out. You’ve done all you can but then something or someone lets you down… is your business prepared for operational compromise?
Victims of cyber attack are not limited to large corporates – they just get the media attention. In fact, if you’re a small or medium-sized enterprise there’s around a 1 in 2 chance that you’ll experience a cyber security breach (source: Sarah Lyons, NCSC Deputy Director). And, if you rely on sensitive and time-critical data, the impact can be just as significant as it was for Garmin, TalkTalk or BA, simply on a smaller scale.
Analysis demonstrates that organisations with well-designed, and rehearsed, contingency plans survive cyber-attack far better than those without. This is what cyber ‘resilience’ is about.
This paper aims to explain how SMEs can also prepare to survive a cyber incident, by following a few simple steps.
From the IT department to the boardroom – cyber as an operational risk
The potential impacts of cyber-attack on ‘UK Plc’ have grown exponentially over the last decade, with our vital infrastructure and data being exposed to the expertise and determination of ‘bad actors’ across the globe. Over time it has become increasingly obvious to business, government and regulators that – in addition to preventing attacks – organisations must become more resilient to them should they occur.
Across the UK’s critical infrastructure and financial systems, operational resilience to cyber compromise has been matured and tested to breaking point. Regulators have harried the sectors they govern, and the concept of cyber insurance has taken root.
Today, cyber risk is firmly embedded within standard operational risk models and its management will doubtless continue to evolve.
However, the story does not end there as the concept of planning ahead for cyber compromise should also be applied to smaller businesses.
With over 60% of cyber-attacks aimed at small to medium sized organisations, and potentially fewer resources available to respond to compromise, SME cybercrime represents a potentially significant risk to the UK economy – even if it does garner fewer headlines.
How improving cyber-resilience protects your business
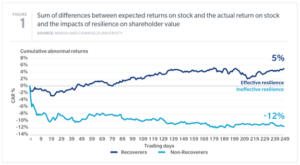
As a Marsh & McLennan / Cranfield study (source: Marsh & McLennan / Cranfield University) shows in this graph, mature cyber resilience significantly improves an organisation’s recovery from attack.
Simply put, the organisations which thrived were those which had prepared and rehearsed for compromise.
Although the scale and complexity is obviously different, there is no reason why the key lesson learned in large companies cannot be taken on board at the SME level – contingency planning can significantly improve how well your company survives an attack.
Cyber contingency planning – hope for the best, prepare for the worst
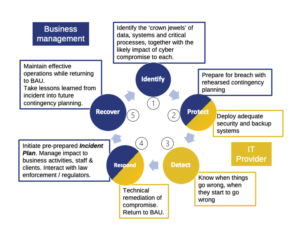
Contingency planning in the cyber world has fundamentally the same aim as the traditional business continuity model – keep the business running in an emergency. The difference is the the nature of the compromise – it’s not about buildings or people, it’s about data and systems. Not where the job gets done or by who, but if at all.
To adapt to this recent phenomena, management need to understand the technical aspects but the ‘plan – react – learn’ cycle depicted below could be adapted to most traditional operational risks.
Stages 1 & 2 are at the core of cyber contingency planning, and are what any SME can do to ensure stages 4 & 5 are effective. What this model also clearly illustrates is that – whilst the IT function has a core role in protecting the business and repairing the damage – it cannot prepare the business itself or manage an incident from a business perspective.
Contingency planning in SMEs need not be complex or arduous. Effective plans can be built around a simple three-step model.
1. Identify what you need to protect the most
Firstly, you need to identify your critical business processes, the technology which delivers them and the data which underpins them. In other words, the ‘crown jewels’ of your business.
Then you need to evaluate the impact to your business if a such process was compromised, and how much that impact worsens if the compromise persists.
Would the worst problem be a loss of availability, confidentiality or data integrity? And what would the impact be? Perhaps direct financial losses or loss of market share. Maybe reputational damage or regulatory sanction.
This long-established risk management approach is known as Business Impact Analysis and is essential to give focus to your contingency planning.
2. Analyse the threat vectors
Which existential cyber threats are most dangerous to your crown jewels? If, for example, a business process is absolutely time-critical, then a loss of availability has the biggest impact, and ransomware or denial of service attack would be the highest threats.
If, however, you are handling highly sensitive customer data, a breach of confidentiality would be the most damaging, with internal malpractice or accident representing likely threat vectors.
Or, if the accuracy of data is essential – perhaps in payment systems – a compromise to its integrity is what really counts and you would perhaps be concerned about malware corruption of data or hacking.
By aligning the most critical impacts to the most likely threat vectors, you create the base on which you can construct likely compromise scenarios, in turn from which you will develop response mechanisms.
3. Plan for compromise and rehearse those plans.
Incident management planning involves trying to envisage the kind of questions you’d be asking yourself if, one Monday morning, you lose all access to your business data or systems.
You would need to determine, and quickly;
• What has happened and what the impacts may be;
• Whether those impacts will worsen with time;
• Who is in charge of the situation;
• Who else needs to be involved (internally and externally);
• What are the most urgent tasks, and what can wait;
• Who might need to be informed (clients, suppliers, regulators etc);
• Whether law enforcement or legal advice is appropriate;
• What manual workarounds are available – how to keep the business going
And, as you start to recover;
• What caused the compromise and whether there were control failures;
• What can be done to lessen the chances of re-occurrence;
• Where management of the incident did not go according to the plan and how the latter needs to change
In addition to giving a clear framework for handling an incident, the plans will also allow continued access to vital data, such as contact information – possibly in printed format or stored off network.
Once you have produced your plan, you will need to ‘scenario test’ it;
• Walk through the plan step-by-step with all relevant stakeholders;
• Challenge each element with “but what if” questions – always presuming that the worst could happen even if unlikely.
Cyber contingency planning – How we can assist SMEs build resilience
The most important things that we bring to this exercise are proportionality and pragmatism. There is no need to over-complicate this in smaller firms with simpler structures so we do not approach projects as some, more traditional, consultancies might. For example, the Business Impact Analysis stage is usually completed with a self-assessment questionnaire, keeping time and costs to a minimum.
If you would like to ask any questions about protecting your business from cyber-attack, or how we might assist, please feel free to get in touch for a no-obligation discussion.
Michael Brunker CISM CIPP/E
Principal – BRP Consulting
Collaboration Partner – The Brooke Consultancy

 Winter 2021
Winter 2021